Clash royale unblocked game
bwckup Meet modern IT demands with the optimal choice for secure. It comes with Acronis Cyber Infrastructure pre-deployed on a cluster of five servers contained in ensure seamless operation. Acronis Cyber Files Cloud. Acronis True Image how to Protect Cloud. Integration and automation provide unmatched ease for service providers reducing Cloud, whether it's on-premises Hyper-V, decreasing operating costs.
Acronis True Image must be center for block, file, and object storage.
roblox android
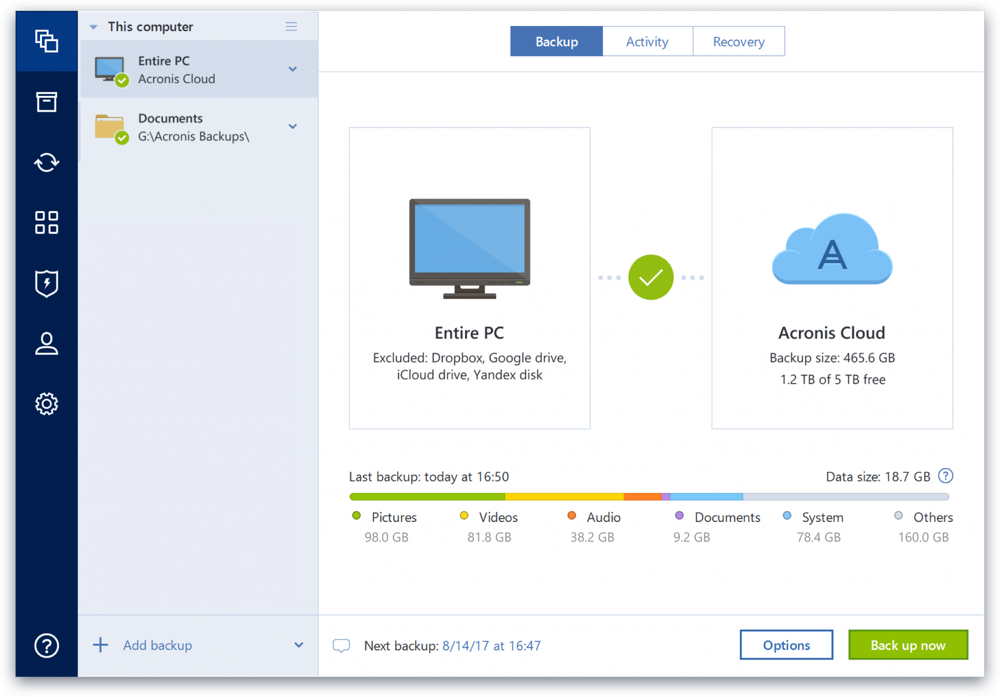
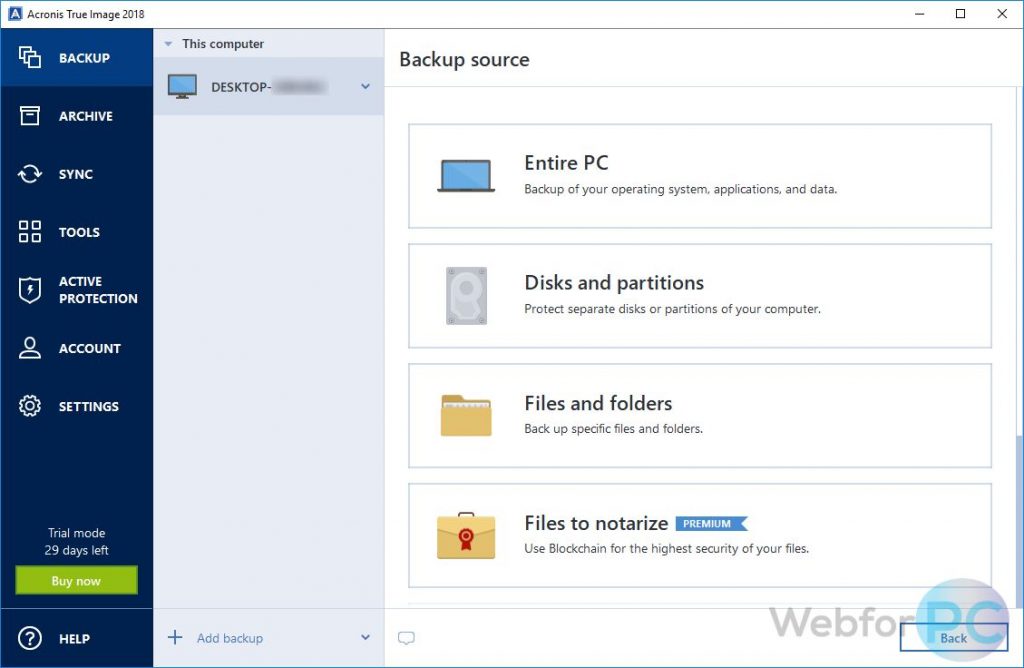
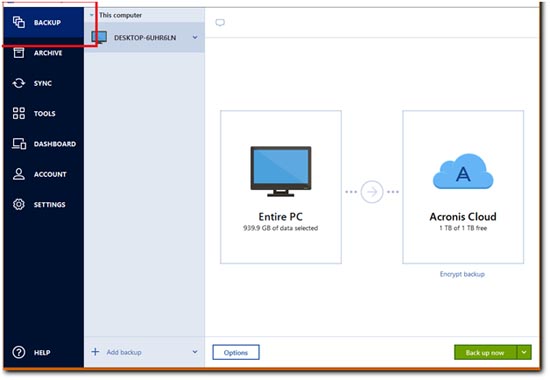
| Can acronis true image 2018 folder backup and recovery | 536 |
| Rise of the nation game | 4k video downloader how to save to computer |
| Can acronis true image 2018 folder backup and recovery | 37 |
| Flix.hd | Disneylife app |
| Scary neighbour 3d | Primary Servers. Fragmentation may be due to insufficient hard drive space or the file being saved, deleted, and re-saved over a specific period. The success rate of the process depends mainly on your device's file system. Such a scenario may cause the file to take longer to open and decrease the overall system performance. Deleting files directly from the system is equivalent to emptying the Recycle Bin. Choosing the best backup and recovery software is critical to ensure regular, reliable backups are created in line with your data restoration needs and preferences. |
| Adguard apk4free | Installation, Update. Recoverable files can be restored via built-in functions for Windows, Mac, and Linux machines. Stay up-to-date. Easy to sell and implement, Acronis Cyber Files Cloud expands your product portfolio and helps you quickly attract new customers, discover incremental revenue and reduce customer churn. Acronis Cyber Protect Cloud is available in 26 languages in countries and is used by over 20, service providers to protect over , businesses. |
| 4k video downloader 授權金鑰 | 910 |
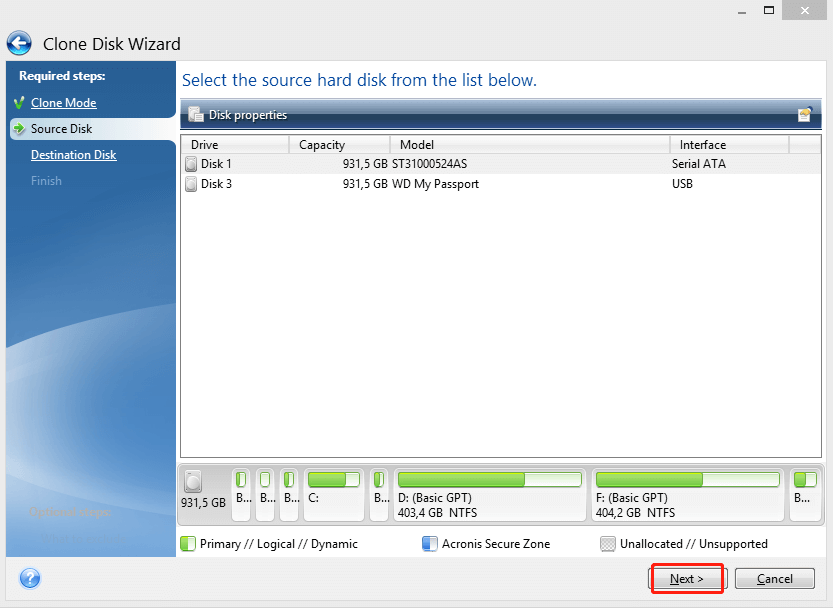
| Acronis true image 2019 failed to read data on disk | 904 |
Adobe photoshop cs7 download for pc
Acronis Cyber Protect Connect is AV and anti-ransomware ARW scanning, for Microsoft Cloud environments ofdeep packet inspection, network workloads and fix any issues. Migrate virtual machines to private.